Million Web Pages Attacked By Lizamoon Malware
More than one million website pages have been hit by a Lizamoon Malware that injects code into sites that redirect users to a fraudulent software sales operation.
The so-called "mass-injection" attack, which experts say is the largest of its kind ever seen, has managed to insert malicious code into websites by gaining access to the servers running the databases behind the Internet, according to the technology security company that discovered it.
Websense, which first found evidence of the attack earlier this week, has called it 'LizaMoon,' after the site to which the malicious code first directed its researchers.
Users can see that they are being redirected when they attempt to visit an infected address, and can close the window with no ill effects.
The attack has largely affected small websites so far with no evidence that popular corporate or government websites have been compromised.
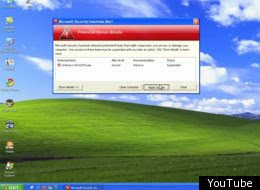
If users do not close the window after typing an infected address, or clicking an infected link, they are redirected to a page showing a warning from 'Windows Stability Center' -- posing as a Microsoft Corp security product -- that there are problems with their computer and they are urged to pay for software to fix it.
Websense said the site appeared to be set up by sophisticated fraudsters out to make money, but it was not clear whether the site also planted malicious software on users' computers if they made a purchase on the site, or if the operation was linked to an identity theft scam.
The presentation of the bogus website, as shown by Websense, is high quality but clearly fraudulent. Microsoft has no product called 'Windows Stability Center". The company did not immediately have a comment on the attack.
Websense said some third-party Web addresses containing information about podcasts available on Apple Inc's iTunes service had been compromised, but said Apple appeared to have prevented the malicious links from working. Apple did not respond to a request for comment.
The attack may take some time to be tamed, warned Runald, as researchers first have to identify the software being compromised, and then website operators have to install updated software.
"Attacks like this tend to stay for a very long time," he said. "Once they are onto something, it tends to stay with us. This LizaMoon event won't disappear over a day."
 |
| Lizamoon attack web pages |
The so-called "mass-injection" attack, which experts say is the largest of its kind ever seen, has managed to insert malicious code into websites by gaining access to the servers running the databases behind the Internet, according to the technology security company that discovered it.
Websense, which first found evidence of the attack earlier this week, has called it 'LizaMoon,' after the site to which the malicious code first directed its researchers.
Users can see that they are being redirected when they attempt to visit an infected address, and can close the window with no ill effects.
The attack has largely affected small websites so far with no evidence that popular corporate or government websites have been compromised.
If users do not close the window after typing an infected address, or clicking an infected link, they are redirected to a page showing a warning from 'Windows Stability Center' -- posing as a Microsoft Corp security product -- that there are problems with their computer and they are urged to pay for software to fix it.
Websense said the site appeared to be set up by sophisticated fraudsters out to make money, but it was not clear whether the site also planted malicious software on users' computers if they made a purchase on the site, or if the operation was linked to an identity theft scam.
The presentation of the bogus website, as shown by Websense, is high quality but clearly fraudulent. Microsoft has no product called 'Windows Stability Center". The company did not immediately have a comment on the attack.
Websense said some third-party Web addresses containing information about podcasts available on Apple Inc's iTunes service had been compromised, but said Apple appeared to have prevented the malicious links from working. Apple did not respond to a request for comment.
The attack may take some time to be tamed, warned Runald, as researchers first have to identify the software being compromised, and then website operators have to install updated software.
"Attacks like this tend to stay for a very long time," he said. "Once they are onto something, it tends to stay with us. This LizaMoon event won't disappear over a day."
Subscribe to:
Post Comments (Atom)




Currently have 0 Response to 'Million Web Pages Attacked By Lizamoon Malware'